- Consulting
- Training
- Partners
- About Us
x
Azure PaaS Services such as Storage accounts, Webapps, and SQL Database are public services with public endpoints, meaning traffic and connectivity are routed over the internet to these public services. But there may be instances where there is a need to have secure connectivity (over Azure backbone network) to these public endpoint services. We will discuss one of many Azure services that will fulfill this need.
Today, I will show you the features and functionalities of Azure Service Endpoints and steps to access Azure Storage accounts from a VM privately using the same. We will also see how to use Azure service endpoint policies to restrict access to two storage accounts.
Before we go ahead and understand the working of Service endpoints, we need to have a few resources in place. We will need to have one Windows VM and two storage accounts to understand the working of service endpoint policies.

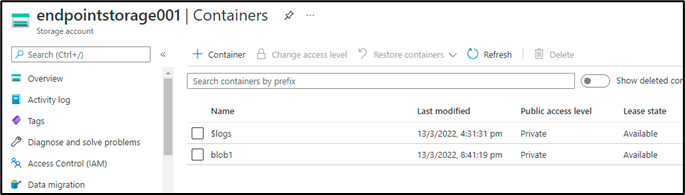
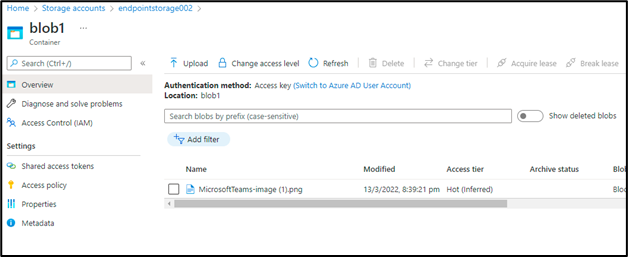







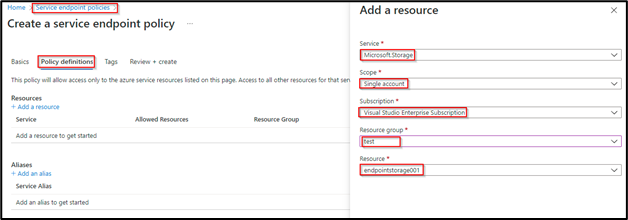
This section will go over a scenario for service endpoints with storage accounts. Azure storage accounts usually have multiple redundancy options such as LRS (Locally Redundant storage), ZRS (Zone Redundant Storage, and GRS ( Geo-redundant storage). So, in GGRS-based redundancy, when we store data in a storage account, another copy of data is created and stored in another pair region.
So if we have a service endpoint in place from one virtual network to connect to the storage account in the primary region say “East US “and this region goes down then connectivity to the secondary pair region say “Central US” can’t be done through service endpoint. So to have access to our data in the Backup storage account in the secondary region, “Central US “, we need to have another virtual network in place and a new service endpoint, a new VM to have secure access to this backup Storage Account.
Today we have seen ways to restrict public access to Azure storage accounts (Azure PASS service) and connect privately over the Azure backbone network. There are other options, too, such as Azure Private endpoints and private links, which provide several capabilities to connect to resources privately which would be part of the discussion for some other day.
CloudThat is the authorized AWS Well-Architected Partner, helping other businesses build secure, high-performing, resilient, and efficient infrastructures for their application and workloads.
CloudThat is also the official Microsoft Gold Partner, AWS Advanced Consulting Partner, and Training partner helping people develop knowledge of the cloud and help their businesses aim for higher goals using best in industry cloud computing practices and expertise. We are on a mission to build a robust cloud computing ecosystem by disseminating knowledge on technological intricacies within the cloud space. Our blogs, webinars, case studies, and white papers enable all the stakeholders in the cloud computing sphere.
Drop a query if you have any questions regarding Microsoft Azure Service Endpoints, Virtual Machines and storage accounts, or consulting opportunities, and I will get back to you quickly. To get started, go through our Expert Advisory page and Managed Services Package that is CloudThat’s offerings.
Q1. What is the cost that we will incur for enabling service endpoints?
Ans: There is no cost associated with using service endpoints.
Q2. If all services in Azure reside within a Vnet why do we need a service endpoint?
Ans: Not all services of Azure reside inside a VNet, Some services such as Azure Storage, Azure SQL, and Azure Cosmos DB are outside Vnet. Hence to have private connectivity from services inside a Vnet we make use of service endpoints.

Our support doesn't end here. We have monthly newsletters, study guides, practice questions, and more to assist you in upgrading your cloud career. Subscribe to get them all!
Comments