- Consulting
- Training
- Partners
- About Us
x
TABLE OF CONTENT |
| 1. Introduction to Amazon’s Secret Manager |
| 2. Features |
| 3. Steps to Configure AWS Secrets Manager |
| 4. Conclusion |
| 5. About CloudThat |
| 6. FAQs |
When you create a custom application to retrieve information from a database, you would typically embed the credentials, or secret, for directly accessing the database in the application. When the time comes to rotate the credentials, you have to do more than create new ones. You needed to spend time updating the application to use the new credentials. The updated application was then distributed. If you had multiple applications that shared credentials and failed to update one of them, the application would fail. Because of this risk, many customers choose not to rotate credentials regularly, effectively substituting one risk for another.
The diagram below depicts the most basic scenario. The diagram shows how you can save database credentials in Secrets Manager and then use those credentials in an application to access the database.
Secrets Manager enhances your security posture by removing hard-coded credentials from your application source code and not storing credentials within the application. Storing the credentials in or with the application exposes them to compromise by anyone who has access to your application or its components. In addition, this process makes rotating your credentials difficult because you must update your application and deploy the changes to every client before you can deprecate the old credentials.
Amazon Secrets Manager allows you to replace stored credentials with a runtime call to the Secrets Manager Web service, allowing you to retrieve them dynamically.
Secrets Manager allows you to store text in a secret encrypted secret data component. This usually comprises the database or service’s connection information. These parameters may include the server name, IP address, port number, and the user name and password used to access the service. The protected text doesn’t include:
Secrets Manager encrypts a secret’s protected text using AWS Key Management Service. AWS KMS is used for key storage and encryption by many AWS services. When your secret is at rest, AWS KMS assures its safe encryption. Every secret is associated with a KMS key in Secrets Manager. It can be either an AWS-managed key for the account’s Secrets Manager or a customer-controlled key created in AWS KMS.
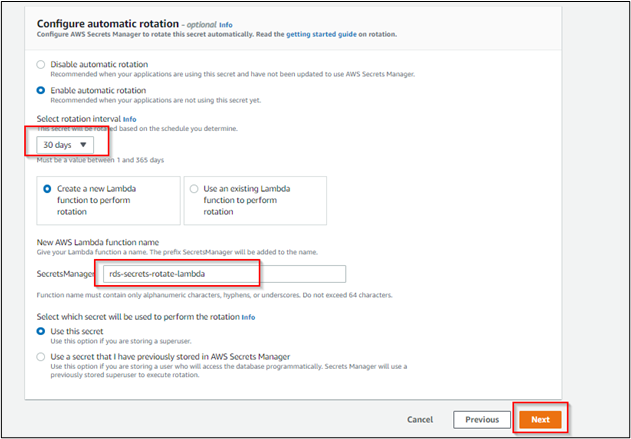
Secrets Manager automatically rotates the secrets without any user intervention, and rotation will happen on schedules
Rotation of the secrets will be implemented using the AWS Lambda function, and this function defines how Secrets Manager performs the following tasks:
The below mention types of databases are supported for configuring secrets and ready-to-use rotation








AWS Secrets Manager allows you to replace hardcoded credentials, such as passwords, in your code with an API call to Secrets Manager to retrieve the secret programmatically. Because the secret no longer exists in the code, this helps ensure that it cannot be compromised by someone examining your code. You can also set Secrets Manager to rotate the secret on a predefined schedule. It allows you to replace long-term secrets with short-term ones, significantly lowering the risk of compromise.
The configured secrets can be embedded into any database application to provide an additional layer of security for your databases. AWS Secrets Manager is also in compliance following various security standards protocols like HIPAA, PCI, ISO, SOC, FedRAMP, etc.,
CloudThat is the official AWS (Amazon Web Services) Advanced Consulting Partner and Training partner and Microsoft gold partner, helping people develop knowledge of the cloud and help their businesses aim for higher goals using best in industry cloud computing practices and expertise. We are on a mission to build a robust cloud computing ecosystem by disseminating knowledge on technological intricacies within the cloud space. Our blogs, webinars, case studies, and white papers enable all the stakeholders in the cloud computing sphere.
CloudThat is a house of All-Encompassing IT Services on the Cloud offering Multi-cloud Security & Compliance, Cloud Enablement Services, Cloud-Native Application Development, OTT-Video Tech Delivery Services, Training and Development, and System Integration Services. Explore our consulting and expert advisory services here.
1. How will my application make use of these secrets?
To begin with, create an AWS Identity and Access Management (IAM) policy that allows your application to access particular secrets. Then, in the application source code, replace plain-text secrets with code to get these secrets programmatically using the Secrets Manager APIs.
2. How does AWS Secrets Manager handle database credential rotation while minimizing the effect on applications?
AWS Secrets Manager allows you to arrange database credential rotation. This allows you to adhere to security best practices and rotate your database credentials adequately. Secrets Manager utilizes the super database credentials you gave to create a clone user with the same rights but a new password when you start a rotation. Secrets Manager then sends the clone user information to databases and apps, which get the database credentials.
3. Will changing database credentials affect open connections?
No. When a connection is established, authentication takes place. The open database connection is not re-authenticated when AWS Secrets Manager rotates a database credential.
4. How can I find out when AWS Secrets Manager rotates a database credential?
When AWS Secrets Manager rotates a secret, you may set up Amazon CloudWatch Events to get a notice. You may also use the Secrets Manager console or APIs to discover when Secrets Manager last rotated a secret.
Our support doesn't end here. We have monthly newsletters, study guides, practice questions, and more to assist you in upgrading your cloud career. Subscribe to get them all!
Comments